Autoruns to Deal with Windows Performance, Startup Processes and Malware
Windows is ranked top in popularity with software developers. According to Statista, in 2019 the number of software developers in the world is estimated at around 23.9 million and is predicted to reach 28.7 million by 2024. However, Windows is also one of the most challenging Operating Systems (OS) to maintain. Over time, it becomes sluggish and inoperable due to an overwhelming number of software installs, overlapping Operating System DLL, Kernel/COM objects, etc. It is also the most targeted OS in the world for malware.
Modern malware developers have implemented sophisticated ways to inject unwanted code through options like Browser Objects, Services, Drivers, Scheduled Tasks, Image Hijacks and AppInit. Checking for each of these conditions requires an expert with extensive knowledge of the underline Operating System; therefore using Autoruns is best to tackle these various issues.
Autoruns is one of the most comprehensive utilities to identify programs that start at system bootup/login, with the capability to check for many other default built-in Windows applications such as Windows Explorer, Internet Explorer, AppInit etc. Features like KnownDlls, Winsock Providers, LSA Providers, Printer Monitors, WMI, Network Providers, Scheduled Tasks, Services, Codecs and Boot Execute illustrate an extensive arsenal and a powerful product.
Autoruns Interfaces and Features
Once the interface is loaded, you will see many of tabs and a list of things that are being started automatically on your computer. The “Everything” tab shows everything from all other tabs within the program, which can be overwhelming and confusing. Instead of looking at the “Everything” tab, I would recommend to just go through each tab separately.
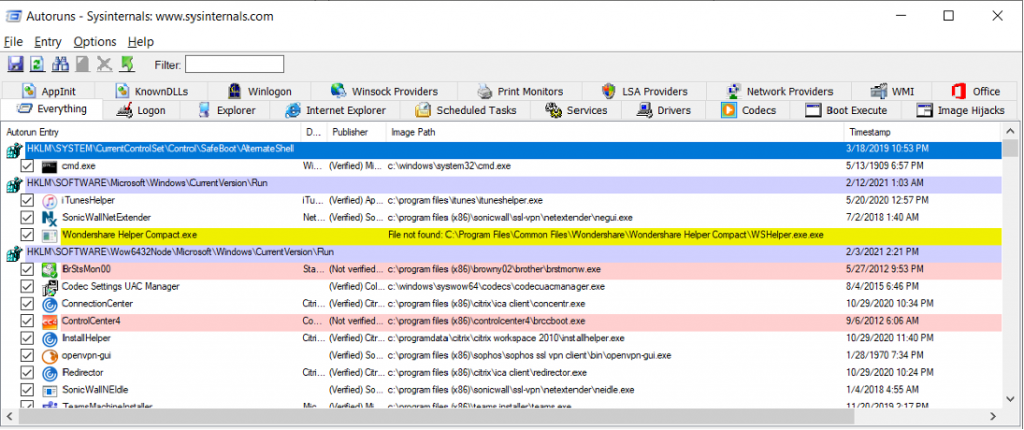
To disable any item in the list, you just need to remove the checked box while manually scrubbing through the list and remove anything that you do not need or recognized.
Autoruns, by default, hides everything built into Windows that is set to start automatically. You can enable or disable this by selecting the desired configuration from the menu “Options” as illustrated.
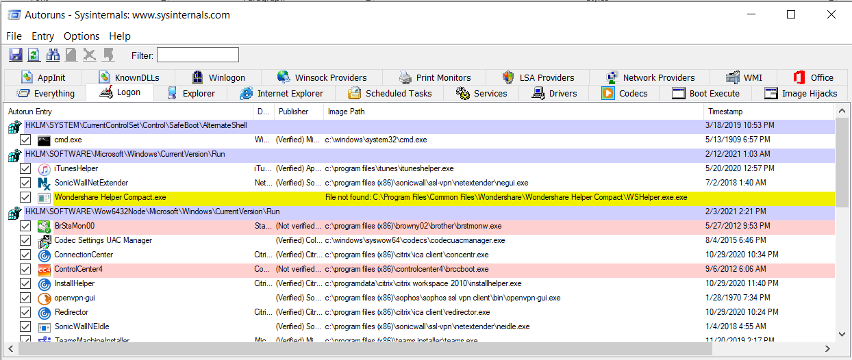
Log-on
This tab checks for things that are loaded automatically at log-on including the Run, RunOnce, Start Menu Folder and Installed Components.
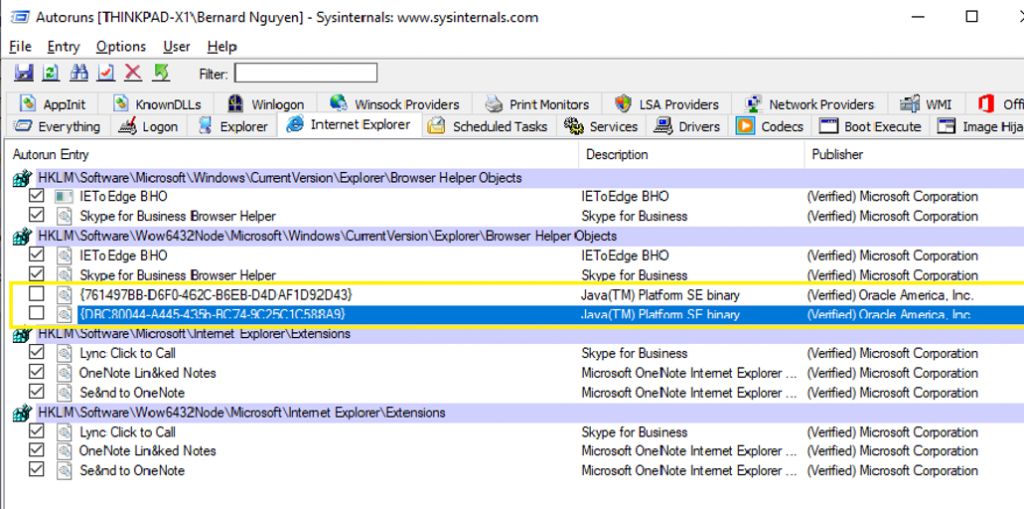
Internet Explorer
This tab displays a list of all browser base extensions, browser helper objects and toolbars that auto load at logon and commonly used by malware and adware. Disable any unknown objects that you do not recognized by unchecking here.
Scheduled Tasks
This tab displays a list of all running scheduled tasks on your system. This is also one of the most problematic during troubleshooting as it continuously manifests itself by creating a loop to reinstall the unwanted code, causing all sorts of nefarious things. Going through the list and unchecking everything that you do not recognize is best practice.
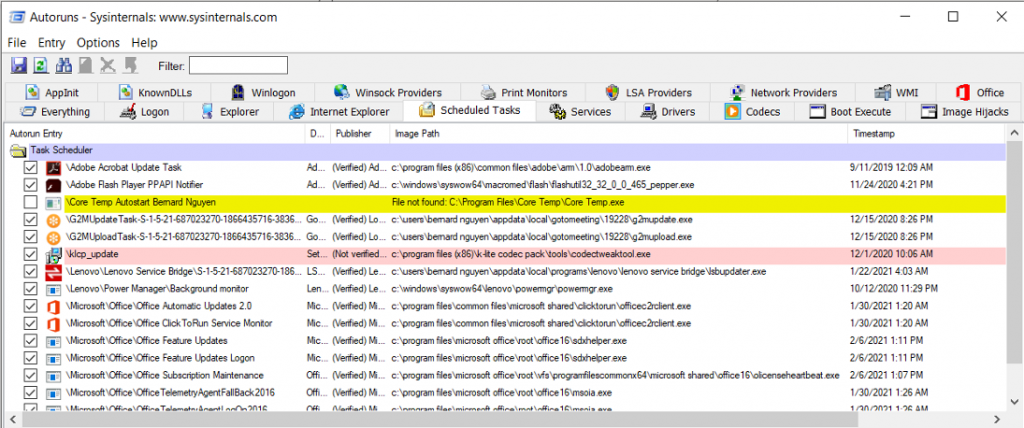
Services
Malware commonly impersonates as a Windows registered services and can be hard to troubleshot and detect.
This tab displays a list of all running services which can be easily disabled by going through and unchecking any non-recognizable software. You may want to be a little cautious when disabling any services as some may be legit and necessary. Be sure to cross-reference the service with the “Description” and “Publisher” column.
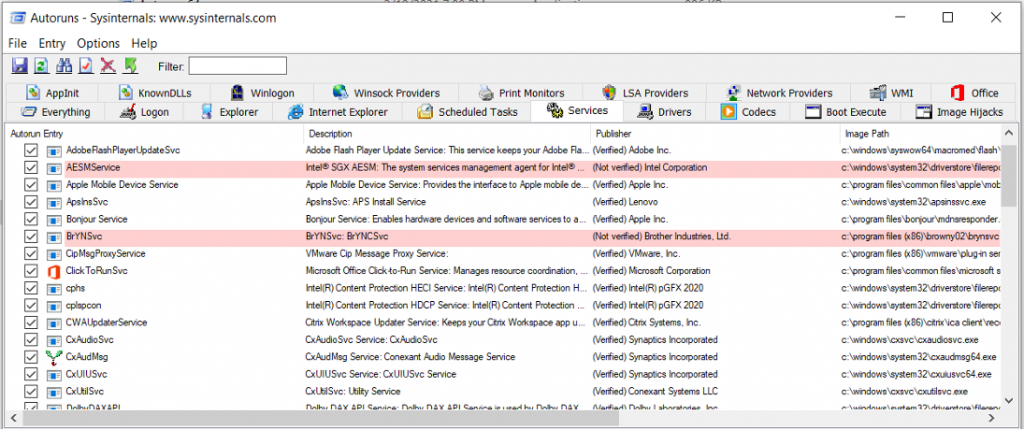
Drivers
Some modern spyware use a device driver that it creates and is very hard to detect. This tab lists all installed device drivers actively executed at log-on. Be extra cautious when dealing with device Drivers and only disable something that is most likely tied to spyware. Disabling the wrong drivers could result in system malfunction so do your due diligence and research. Right-click on each unrecognized driver and select the search online from the menu or hit “CTRL+M”.
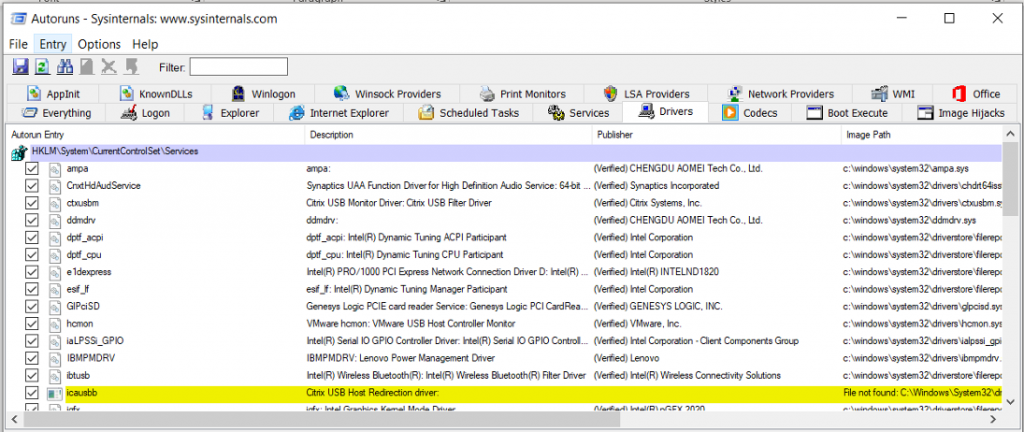
Codecs
These are libraries of code that are used to handle media playback for videos or audio, and unfortunately they have been abused by malware to automatically start on the computer. You can disable them here if necessary. Where applicable, disable any that do not have Description and Publisher listed.
Boot Execute
This tab lists items that start automatically during system boot time such as a scheduled hard disk check.
Image Hijack
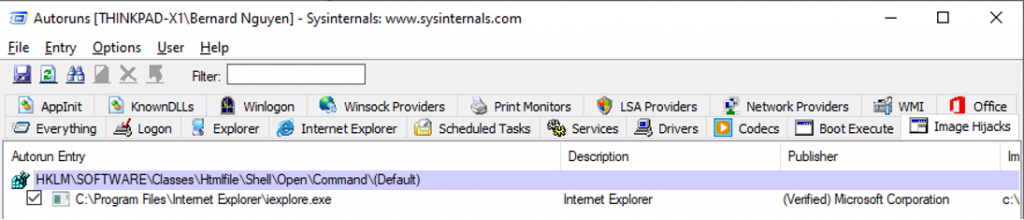
The Image Hijack tab lists registry settings that switch and control how a certain program is loaded, including hijacking all executables and running them through another process, or even assigning a “debugger” to any desirable executable. This is also another common method Malware developers use to block you from loading software like Malwarebytes or any other anti-malware tools.
An example illustrated registry value configured to switch “AcroRd32.exe” with “ProcessHiJack.exe” when this program loaded.
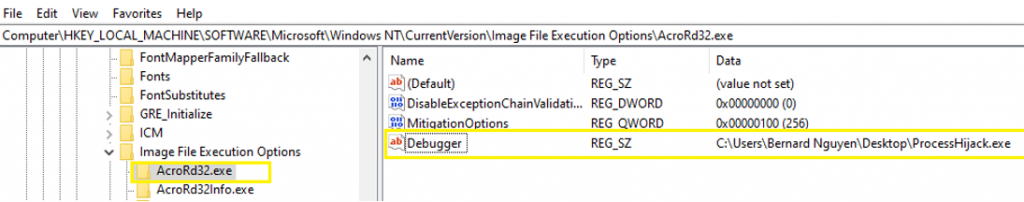
Note: If you see anything in the Image Hijacks tab other than the values for Process Explorer, you should immediately disable them.
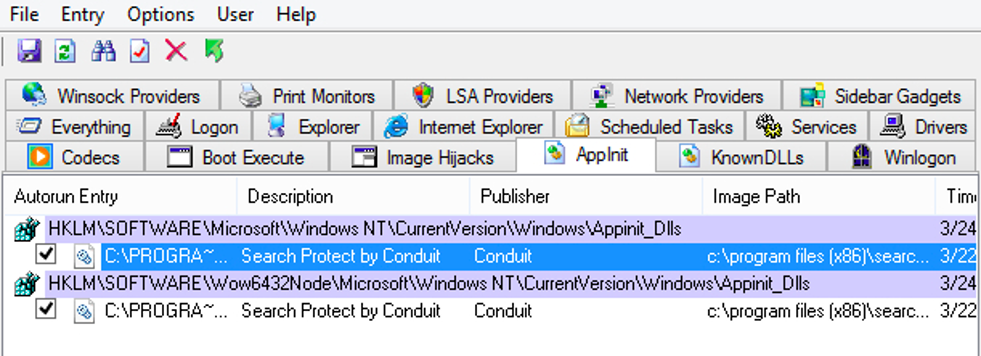
AppInit
When an application loads the “user32.dll” library in Windows, the “AppInit” checks for registry value and registers the related DLLS found. Once loaded, it then allows the affected application to be hijacked by Malware. With more recent Windows versions, Microsoft locked this down and required the effected DLLs to be Digitally Signed.
The one exception is if the RequireSignedAppInit DLLs key is set to 0, therefore allowing Windows to process and load the targeted program automatically.
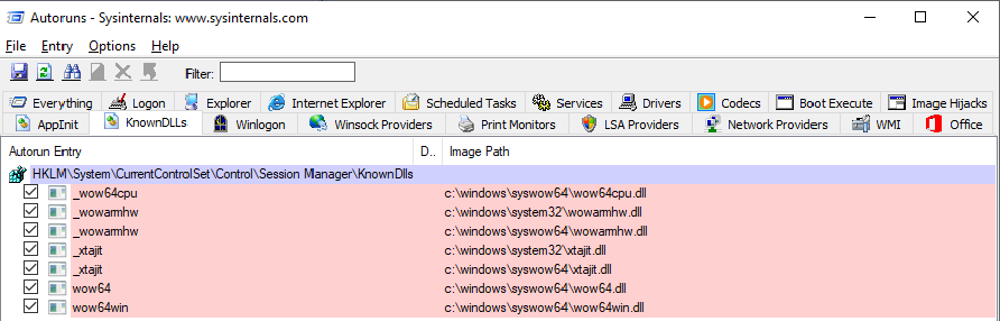
KnownDLLs
The “KnownDLLs” tab displays specific DLL file and version automatically loading at logon and is intuitive. Manually scrub through the list and uncheck anything that you do not need or recognize.
Winlogon, LSA Providers & Print Monitors
In most cases, Winlogon and LSA Providers tabs are typically null and empty as it simply displays any applicable add-ons that extend various aspects of the Windows system. However, it is necessary to check them as best practice. The Print Monitors tab lists third-party applications that may have an impact to the printer.
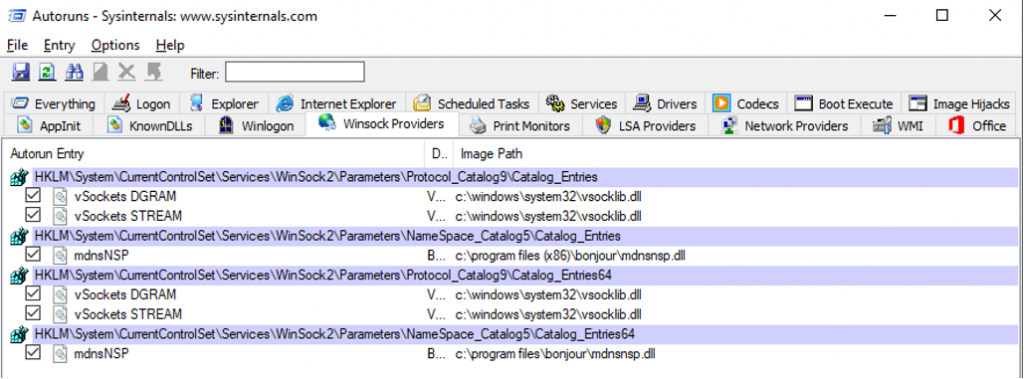
Winsock & Network Providers
The “Winsock” and “Network Providers” tab lists services related to networking. This is useful when you need to troubleshoot network and internet connectivity as conflicting Winsock services could be the culprit.
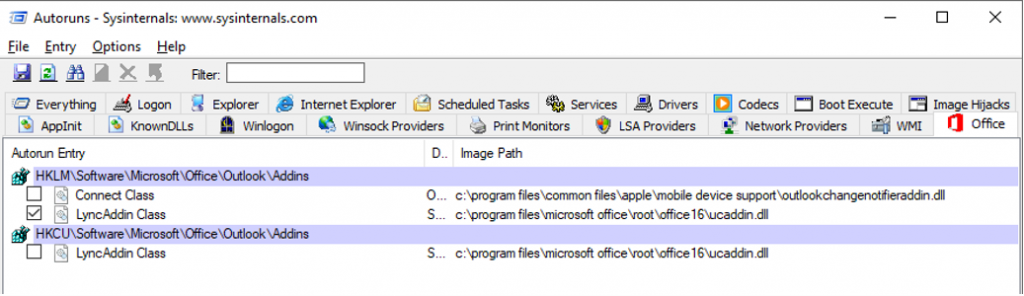
Office Tab
Finally, the “Office Tab” lists Microsoft Office related registry keys and associated DLL image path. This is very handy when used to identify Microsoft Office Suite undesirable behavior.
Disclaimer
The software is provided "AS IS" without any warranty, either expressed or implied, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. The author will not be liable for any special, incidental, consequential, or indirect damages due to loss of data or any other reason.
